論説

概要
- Amid warnings of increased malicious activity from Russia-linked groups, companies must swiftly get the cybersecurity basics right and avoid underspending on this critical function.
- Companies with direct-but-dormant exposure to Russia face additional complications, while all executive teams will have to be on their guard against intellectual property theft.
- The most resilient businesses will go beyond checklist-focused implementation of industry frameworks, nurturing strategic capabilities that evolve with shifting cyber threats.
Cybersecurity is increasingly seen as risk No. 1 by large businesses—and with good reason. Even before the Russian invasion of Ukraine escalated the threat posed by hackers, cybercrime was costing the world an estimated $6 trillion annually according to Cybersecurity Ventures, through malign actions such as ransomware attacks, data destruction, embezzlement, and theft of intellectual property.
By their own admission, many companies aren’t ready to contain this rising threat. When we surveyed executives on the topic, only 43% felt that their company followed cybersecurity best practices. Yet even that lowly figure looks like an overestimate. Deeper analysis of our survey sample showed that only about 24% actually met the best practice threshold. On a cybersecurity maturity scale of 1–5, a typical company is likely to rate only 1.5–2.5: way too low.
With the heightened threat unlikely to ease soon, many companies need to refocus on getting the cybersecurity basics right. However, a truly strategic response to today’s dangers will require much more than a tactical alignment with industry norms. Over the coming months, the most resilient companies will also build and refine the capabilities needed to keep improving their defenses against the evolving situation in Russia and Ukraine—and against fresh threats yet to emerge.
First things first: Get the basics right
Ukraine-related cybersecurity incidents have been numerous both before and during the invasion, including distributed denial-of-service attacks, data-wiping malware, and website defacement. According to Microsoft, sustained pre-invasion cyber operations against Ukraine by groups aligned with Russia began as early as March 2021, ahead of intensifying activity that included more than 230 observed cyberattacks in Ukraine from December 2021 to March 2022.
The impact of the hostile activity has been international. For instance, when a satellite-based Internet service suffered a cyberattack subsequently blamed on Russia, the outage hit tens of thousands of customers across Europe, not just Ukraine, and also affected German wind turbines. More than 90% of Russia-based attacks observed in Microsoft’s online services in 2021 were aimed at NATO member states, particularly the US, the UK, Norway, Germany, and Turkey.
More online attacks are expected to follow. The US and other countries have warned companies inside and outside the conflict zone to brace themselves for increased malicious cyber activity from Russia-linked groups, in retaliation for sanctions and international support for Ukraine. The European Union said cyberattacks against Ukraine “could spill over into other countries and cause systemic effects, putting the security of Europe’s citizens at risk.”
In response, companies should understand and swiftly act on government advisories. In the US, that includes communications from the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), and the National Security Agency (NSA). Companies outside the US should look to the local equivalents, many of which have been involved in cross-border cooperation.
The absence of critical security patches is at the root of many breaches. As well as rigorously checking that patches are applied in a timely fashion, companies need to ensure that employees (particularly the high-value targets at the top of the organization) know how to identify and avoid malware-laced emails and other threats.
Other basic hygiene measures include enforcing multifactor authentication, conducting extensive vulnerability scans, and instigating a general hardening of the technology environment (for instance, by shutting down unneeded services or ports).
Gauging the right level of spending and investment in cybersecurity is critical—a challenge that includes ensuring that there are enough skilled cybersecurity professionals on the payroll. Our research and experience show many companies underinvest significantly (see Figure 1), which leaves them underprotected and prone to a range of issues, such as incomplete or outdated cyber-protection technology and inadequate training for both cyber specialists and general employees.
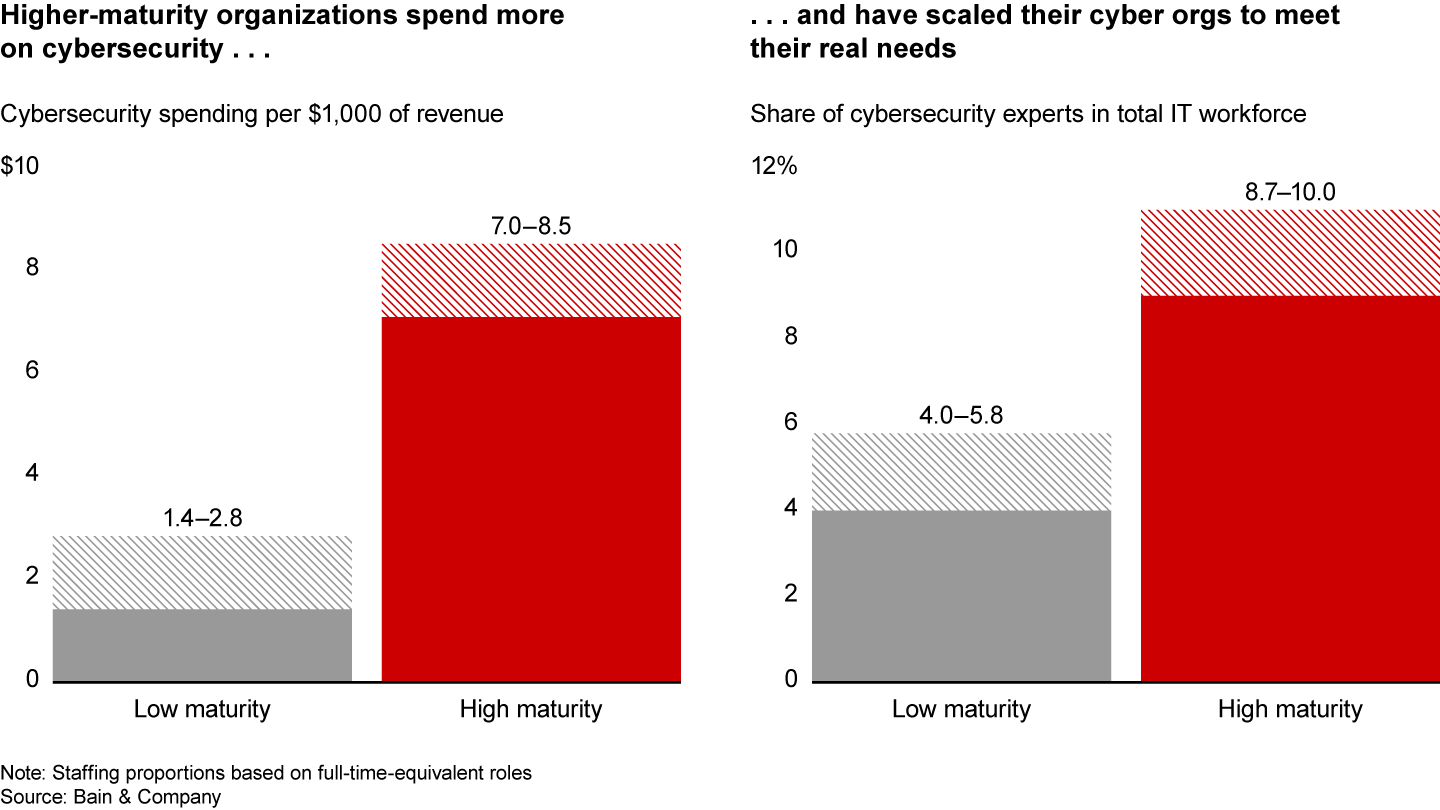
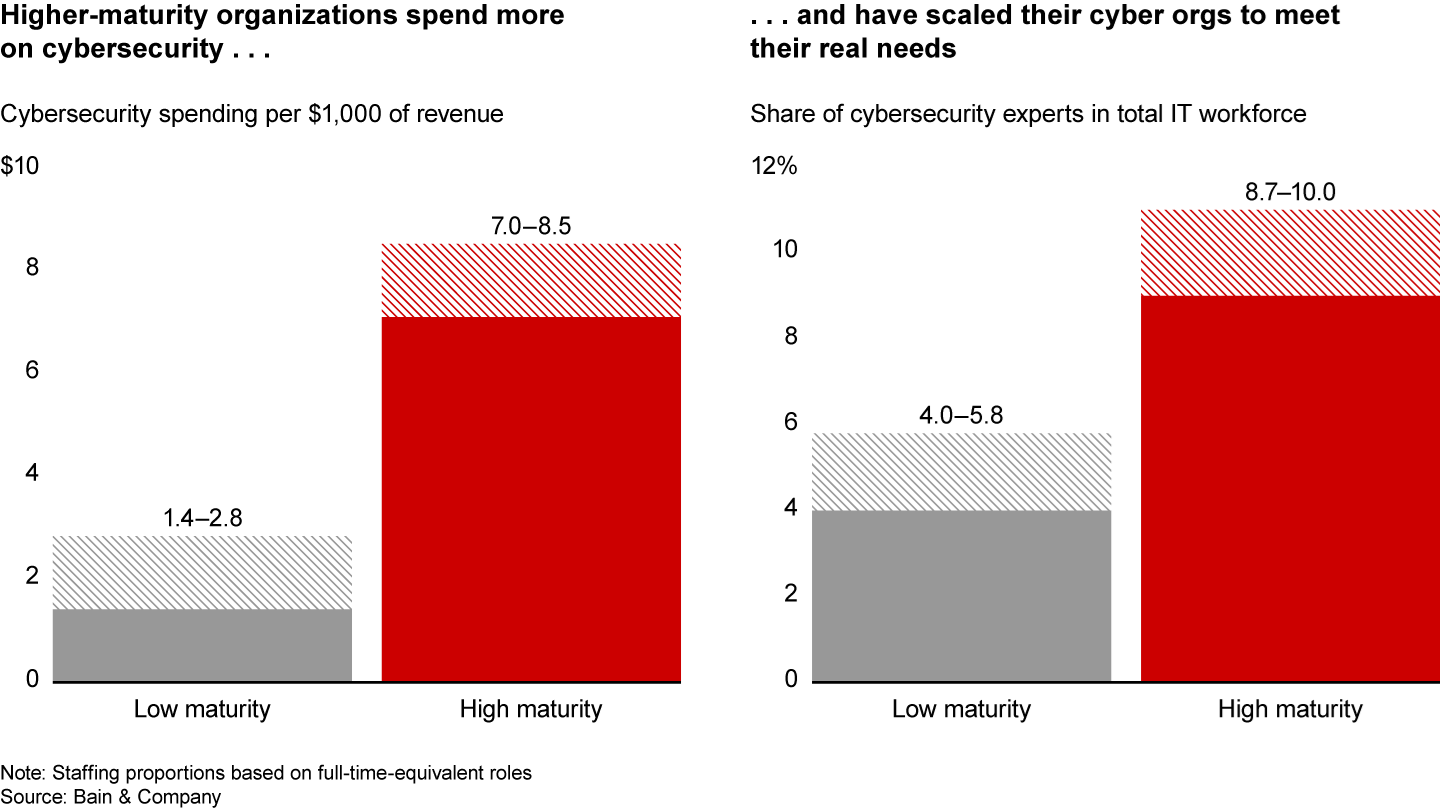
Amid all this defensive preparation, there should be an understanding that digital assets will be breached at some point, and that business continuity plans will need to be activated so that critical services can continue. That means ensuring that incident response playbooks are fit for purpose and tested.
Complications for directly exposed companies
Getting the basics right will be different for companies that still have direct exposure to Russia, including multinationals that have continued to pay local employees after halting operations. This kind of residual involvement is likely to create cybersecurity complications beyond the obvious risk of direct attacks by hacktivists and other disruptive actors.
For instance, operationally inactive workers still on the payroll may retain access to company laptops. When it comes to rolling out updates to those computers, employers will need to balance the need to remain protected with the need to observe sanctions. Information-sharing policies may also require modification.
If the Ukraine war stretches on for many months or even years, accompanied by a continuation of sanctions, all companies will need to be on their guard against an increased risk of intellectual property theft, particularly in sectors such as technology, defense, and financial services. Lingering sanctions against Russia could also encourage ransomware attacks, making it particularly vital to heighten oversight of vectors commonly used by ransomware, such as remote desktop sessions.
How to go beyond the basics
Industry frameworks such as NIST and ISO 27002 are an essential building block of cybersecurity. But to protect themselves fully amid such global instability, companies need to go beyond checklist-focused implementation of the best practices enshrined in these frameworks.
For one thing, the guidance in frameworks is often control oriented and high level; the large amount of room they leave for interpretation makes good cybersecurity hard to define. It doesn’t help that events often move fast on the ground while frameworks are updated infrequently. Nor can frameworks give much guidance on the complex trade-offs that management teams must weigh, such as the right balance between organizational speed and security.
Many leading companies are seeking greater long-term resilience by also focusing on building strategic cybersecurity capabilities. This holistic approach recognizes that companies need sophisticated, self-evolving capabilities to effectively manage complex and quickly changing cybersecurity risk.
A good example of what key capabilities look like in practice can be found in the management of third-party cybersecurity risk in the supply chain, which came to the fore early on in the Russian destabilization of Ukraine. (Microsoft observed supply chain vendors in Ukraine and abroad being targeted in mid-2021.) This is a complex area, with large companies typically having thousands of suppliers. These third parties can hold up supply chains if a cyberattack leaves them unable to operate—and they can also propagate the same issues to their customers.
Tackling this area of risk successfully requires that companies:
- identify and classify third parties based on the cybersecurity risk posed and the likely impact (both direct and supply chain related);
- assess third parties both when they are first selected and on an ongoing basis—with in-house teams or through a new breed of external risk assessment service; and
- reduce risk to an acceptable level through measures such as informal persuasion, contract stipulations, additional controls, and supply chain diversification to boost continuity.
This is complicated to do reliably and at scale, which is why many companies end up living with large but unquantified levels of cybersecurity risk. Simply put, there is no shortcut around building the capabilities needed to manage this area of risk effectively. But companies often have more options at their disposal than they realize.
When one consumer packaged goods company systematically tackled the risk presented by third parties, it uncovered a host of practical ways to strengthen its protection. These included improving contractual language, updating its formal policy on cybersecurity requirements for suppliers, clarifying which suppliers were most important to the business, and implementing risk controls and risk mitigation measures such as tighter third-party access to company systems.
The effort and investment required to persuade suppliers to improve their cybersecurity can also lead to broader benefits. For instance, measures taken to mitigate third-party cybersecurity disruption risk (such as boosting inventory of essential manufacturing parts in case of a disabling cyberattack on a supplier) can contribute to a companywide push to enhance operational resilience.
Going beyond the basics is essential if companies are to protect themselves in these hyperconnected and unstable times. Building strong strategic cybersecurity capabilities is the answer.
The authors would like to thank Salman Faiz for his contribution to this brief.